VISUALIZATION OF INFORMATION SECURITY MANAGEMENT PROCESSES
N.G. Miloslavskaya (ORCID 0000-0002-1231-1805), A.I. Tolstoy (ORCID 0000-0001-9265-1510)
National Research Nuclear University MEPhI (Moscow Engineering Physics Institute), Russian Federation
e-mail: NGMiloslavskaya@mephi.ru, AITolstoj@mephi.ru
Content
2. Information security related terms
3. Process and process approach
4. Structure of processes of Information Security Maintenance System (ISMaS)
5. ISMaS planning as a single process
5.1. «Object description» subprocess
5.2. «Assets identification» subprocess
5.3. «IS threat analysis» subprocess
5.4. «Selection of IS threats» subprocess
5.5. «IS threat description» subprocess
5.6. «IS risk treatment» subprocess
5.7. «IS Policy development» subprocess
5.8. «Internal IS documents development» subprocess
Abstract
The article substantiates the need to visualize information about the information security (IS) management processes that help to make informed decisions about their timely adjustment to improve the security of these objects. The structure of the processes of the IS maintenance system (ISMaS) is presented. The main processes of IS management – planning, implementation, control and improvement – are described and their connections with other IS processes are shown. Information on the IS management processes, where its visualization is particularly useful, is determined. The example of the "ISMaS Planning as a single process" process presents visualization of information of all its subprocesses, namely "Object description", "Assets identification", "IS threat analysis", "Selection of IS threats", "IS threat description", "IS risk management", "IS Policy development" and "Internal IS documents development". Two directions of the further research are specified in the conclusion.
Keywords: visualization of information, information security, information security management, management processes, information infrastructure, management system, information security maintenance system.
1. Introduction
While ensuring information security (IS) of any objects, it is relevant to make decisions aimed at maintaining the required IS level. In this case, it is important to create the necessary information base, its layout and presentation in a form that allows the organization’s specialists operating the IS maintenance system (ISMaS) to make effective decisions.
Volumes and heterogeneity of the data to be carefully analyzed further are so large that the issue of its structured, combined (consolidated) and visualized presentation within a single intuitive interface to make timely and justified decisions in the field of IS management for organizations’ assets rises very sharply. Properly designed to the needs of IS departments and administrators, centralized real-time visualization systems of the consolidated information related to the processes of IS maintenance (ISMa) can help in this matter.
The optimal design of visualization system contributes to a deep understanding of the functioning features of ISMa processes in their entirety, focus and effectiveness. Therefore, such systems are useful in the implementation of educational programs for IS professional training.
A developer has to address the three major questions when designing object’s IS information visualization systems: What information is a subject to visualization? How it should be presented on a monitor’s screen? How to interpret the information displayed unambiguously?
The answers to these questions were partially obtained in the study of visualization problems for managing IS incidents in the organization’s information infrastructure (II) [1]. Therein the necessity of visualizing information on IS events and incidents occurring in the organization’s II was justified, and the main processes of IS management (namely, monitoring of IS and management of IS incidents), where visualization of this information is especially useful, were identified. The visualization tasks were formulated and requirements for visualization systems were raised. The examples of security information and event management (SIEM) systems that implement the above requirements and solve these tasks were given (for example, QRadar by IBM-Q1 Labs, HP ArcSight Enterprise Security Manager (ESM), McAfee Enterprise Security Manager and Splunk Enterprise). The urgency of the described solutions in the light of the appearance of IS analytic systems on the market of information protection systems was emphasized.
This article contains the results of our research, which continues the research carried out earlier, but related to a different more general area – IS management and not just IS incident management. At the same time, special attention is paid to the formation of an information base on the object’s ISMa processes, which in accordance with the modern approach are the key ISMa processes [2-8]. The structure of the ISMa processes, their place and the set of data on these processes that are to be visualized are defined. This corresponds to the answer to the first of the three questions posed above, which is the basis for the formation of the visualization system. With an abundance of data, errors in their selection and layout can significantly reduce the effectiveness of decisions related to the answers to the second and third questions.
It is worth mentioning that there are no analogues of the presented research both in Russia and abroad in the open press, therefore there is no “Related work” section.
2. Information security related terms
In general, the "IS" term refers to the fields of science, technics, technology and education related to the security of various objects in the face of threats in the information sphere. Such examples are the IS scientific direction, the educational direction for the IS personnel training, as well as the names of numerous scientific conferences and periodical scientific publications, the integral part of which is the IS term.
In practical applications, the IS term is associated with various concepts and, accordingly, various definitions. In this case, it is necessary to state the fact that the formation and evolution of relations to this term were significantly influenced by the development of information processing technologies on one hand and English terminology on the other hand.
In the process of evolution of information processing technologies, the following terms appeared in the English publications at different times:
· "Data Security" and "Computer Security" in the 1970s;
· "IS", "Information Technology (IT) Security", "Systems Security", "Information Protection" in the 1980s;
· "Network Security" in the 1990s.
In Russia, three terms, namely "information protection", "IS" and "security of information" (SI), are mainly used.
Information protection is an activity aimed at preventing the leakage of protected information, unauthorized and unintended impacts on the protected information [9].
It should be noted that the English term "IS" in the Russian information sources is juxtaposed to two terms: "IS" and "SI", which differ in understanding and definitions.
As for the IS term, it should always be combined with the name of the object. For example, "IS of an organization", "IS of an automated system".
If the object itself is information, IT or informatization objects, the term "IS of the object" is transformed into the term "IS".
Information [data] security refers to the protected information state, which ensures its [their] confidentiality, accessibility and integrity [10].
The central idea in the definition of the "IS of the object" and "SI" terms is the state of protection of the object (information) against threats.
Thus, the following definitions can be adopted:
IS of the object refers to the state of protection of the object against threats in the information sphere.
SI refers to the state of protection of information, which ensures its confidentiality, accessibility and integrity, as well as non-repudiation, accountability, authenticity and reliability.
The latter definition differs from the definition in [9] in that the properties of non-repudiation, accountability, authenticity and reliability are added to the confidentiality, accessibility and integrity properties of information (sometimes referred to the IS properties of the protected object), which correspond to the current state of the IS theory [10].
At present, in the case of IT, the problems of their security are most often combined under the "IS" term (for example, the group of international standards of ISO/IEC 27000 series and their analogue – the group of national standards GOST R ISO/IEC 27000). Therefore, in this article we will be guided by the concept, which is closer to the "SI" term, but we will use the "IS" term, assuming that the IS object is either information, or IT, or informatization objects.
In either case, the definitions of both the “IS” and “SI” terms are related to the state of the object. Ensuring this state is possible when performing certain actions, which represent a set of processes. This involves very important terms:
· "IS maintenance" (ISMa) – processes of maintaining the state of the IS object;
· "IS Maintenance System" (ISMaS) – a set of related ISMa processes, measures (IS controls) and the necessary resources.
In this case, the key concepts are the terms that define the "process" and "process approach" terms. This requires additional explanations.
3. Process and process approach
A process refers to a set of interrelated and/or interacting activities that use inputs to deliver an intended result [11]. A generalized illustration of this definition is presented in Fig.1.
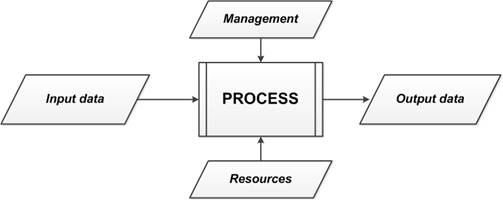
Fig. 1. A generalized illustration of the process concept.
Depending on the context, the "intended result" is called output, product or service. The inputs to the process are usually the outputs of other processes, and process outputs are usually inputs to other processes. Two or more interrelated and interacting processes can be jointly considered as a process [11].
The process as a set of interrelated and/or interacting activities requires certain resources and management impacts. They can also be considered as inputs.
Based on the process’s definition, all actions within the organization can be viewed either as a process (or a business process, as more often called) or its part. The business process refers to a set of one or more time-ordered, logically related and completed activities that together support the activities of the organization and implement its policies to meet the objectives. The business process is usually carried out within the framework of a predetermined organizational structure that describes the functional roles of participants in this structure and the relationship between them.
The process approach refers to the systematic identification and management of business processes used by the organization and especially the interaction of such processes [11].
This approach is based on a view of the organization as a set of key business processes, rather than functional units. The main focus of this approach is on cross-functional processes that combine individual functions into common flows and are generally aimed at achieving the end result of the business, rather than a separate unit. Thus, the main advantage of the process approach is management and control of the interaction between various processes and links in the context of the functional hierarchy (organizational and staff structure) of the organization.
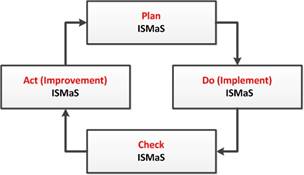
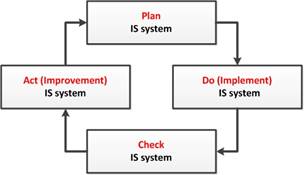
To structure all processes and to ensure that all significant elements of the process approach are taken into account, the cyclic model, or the PDCA (Plan-Do-Check-Act) cycle, or the Shuhart-Deming model is applied. A simplified PDCA cycle is shown in Fig.2.
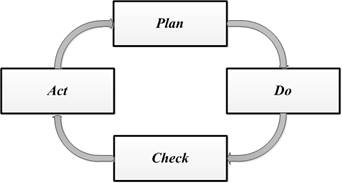
Fig. 2. PDCA cycle.
The application of the PDCA cycle in a wide variety of fields allows the effective management of activities on a systemic basis [12]. This cycle can be applied within each organization’s process, both high-level and simple production processes, as well as to the system of processes as a whole. It is closely connected with the planning, implementation, control and continuous improvement of both the business processes of the organization and other processes related to the activities of the organization, including the ISMa processes.
When visualizing the IS processes, it is important to determine the data related to the input and output of a particular process and to match the input and output data of the associated processes that form the ISMaS for a specific object.
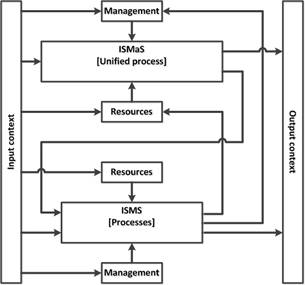
4. Structure of processes of Information Security Maintenance System (ISMaS)
Taking into account the definition of the ISMaS term adopted in this work, the ISMaS structure includes the processes that supports IS, ISMa measures (IS controls), as well as the resources needed for this.
Each process included in ISMaS should be appropriately managed (the generalized structural diagram of the process is shown in Fig.1). The management impact is also a process, which is aimed at ensuring the proper completeness and quality of the process to which it is directed. Therefore, two groups of processes can be distinguished in ISMaS: the ISMa processes and the processes of their management.
The connectivity of these processes allows them to be combined into two systems (Fig.3):
1. IS system – ISS (integrates the ISMa processes; the number of processes is M). ISS is a set of ISMa processes, measures (IS controls) and resources needed to implement these processes [13, 14];
2. IS management system – ISMS (integrates the management processes; the number of processes is N). ISMS is a set of management processes aimed at ensuring the completeness and quality of the ISMa processes (designed to plan, implement, control and improve the ISMa processes), measures (IS controls) and resources needed for these processes [13, 14].
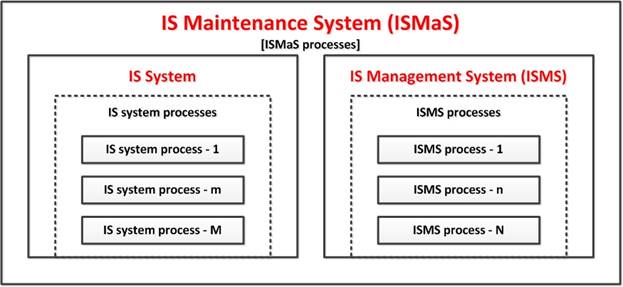
Fig. 3. ISMaS structure.
ISMS should be considered as a part of the object’s management system and is aimed at planning, implementing, control and improving ISMaS. In this case, we apply the process approach associated with the use of the Deming cyclic model (Fig.2), which can be represented as the structural diagrams shown in Fig.4 for managing ISMaS as a single process (Fig.4a) and for managing a separate ISS process (Fig. 4b).
|
a) |
b) |
|
Fig. 4. Structural diagrams for IS management processes implementation. |
|
Thus, two groups of processes can be distinguished in ISMS:
1. IS management processes aimed at ISMa as a single process;
2. IS management processes aimed at a separate process of ISS.
Each process of ISMaS, ISS or ISMS is implemented using a certain set of ISMa measures (IS controls), which can be technical or organizational (including management) [15].
The technical ISMa measure is a measure implemented through the use of hardware and/or software tools and/or systems (technical tools).
The organizational ISMa measure is a measure that is not a technical ISMa measure and which provides the establishment of temporary, territorial, spatial, legal, methodological and other restrictions on the conditions for the implementation of the process.
The ISS processes use mainly technical measures (technical tools), but they can also use organizational measures.
The ISMS processes use mainly organizational measures, but they can also use technical measures (technical tools).
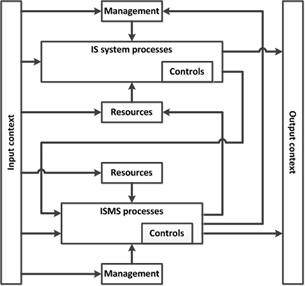
Taking into account the two groups of management processes in ISMS, it is possible to determine the links of these processes with ISMaS as a single process and with separate ISS processes (Fig.5). In the structural diagrams shown in Fig.5a and Fig.5b, each process requires management and resources in accordance with the generalized structural diagram shown in Fig.1. At the same time, the management of a single process representing ISMaS (Fig.5a) or a separate process included in ISS (Fig.5b) provides the management processes that are included in the first and second ISMS groups, respectively. Likewise, management processes can also determine the necessary resources for implementing a single ISMaS process and ISS processes. All the processes in Fig.5a and Fig.5b are implemented using certain ISMaS measures (IS controls).
|
a) |
b) |
|
Fig. 5. Structural diagrams for IS processes implementation. |
|
The input of any process related to ISMaS, ISS or ISMS is data in the context of the conditions of operation of the object and the organization to which the object belongs (the input context). There are external and internal input contexts [2].
The external context of ISMaS implementation as a single process and associated ISMS processes includes data on the external environment of the organization, where the IS object exists (the external environment in which the organization seeks to meet its objectives, including the features of the external infrastructure), as well as legal norms and regulatory requirements, set out in the documents of the higher levels and organizations (state, international, corporate) related to the IS sphere.
The internal context includes information on the internal environment, in which the organization seeks to meet its objectives, as well as information on the features of the functioning of the IS object (for example, its infrastructure description) and the ISMa requirements, set out in the internal documents of the organization.
The output of any process related to ISMaS, ISS or ISMS is characterized by information (data) in the context of the results of the functioning (implementation) of this process (the output context).
The output context can fill the input context for other processes.
The IS management processes aimed at ISMa as a single process belong to the first group of ISMS processes. In accordance with Fig.4a, these processes form the following directions:
1. The "Planning" direction – planning ISMaS as a single process;
2. The "Implementation" direction – implementing ISMaS as a single process;
3. The "Control" direction – control ISMaS as a single process;
4. The "Improvement" direction – improving ISMaS as a single process.
In this article, we will consider the IS management processes related only to the "Planning" direction, in order to determine the structure of input and output data for individual components of the object’s ISMaS as a single process.
5. ISMaS planning as a single process
The "Planning" direction combines all the processes that are necessary for the transition to the "Implementation" direction (Fig.4a). To do this, the data relevant to the input context (internal and external) should be transformed into the data sufficient to implement ISMaS as a single process (Fig.5a). These data extend the internal context of the object and are formed as a set of internal documents of the organization related to ISMaS of the object under consideration. In its essence, the "Planning" direction supports the development of ISMaS. Therefore, this documentation can be attributed to the project documentation for ISMaS.
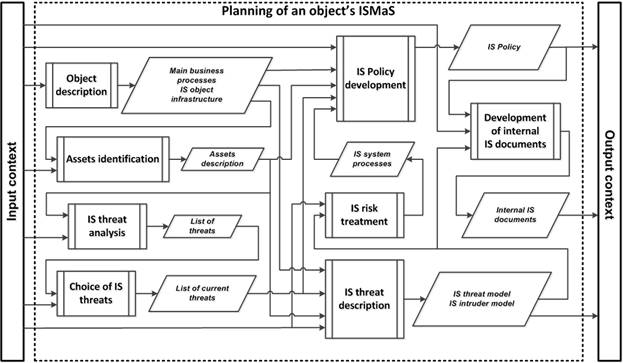
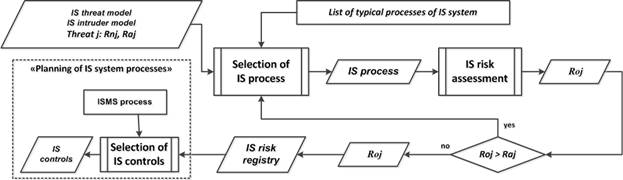
In accordance with the recommendations of standards [2-8], the following list of related subprocesses that should be implemented for the ISMaS development is proposed (Fig.6): "Object description"; "Assets identification"; "IS threat analysis"; "Selection of IS threats"; "IS threat description"; "IS risk management"; "IS Policy development" and "Internal IS documents development".
|
|
|
Fig. 6. Structural diagrams for ISMaS as a single process at the “Planning” direction. |
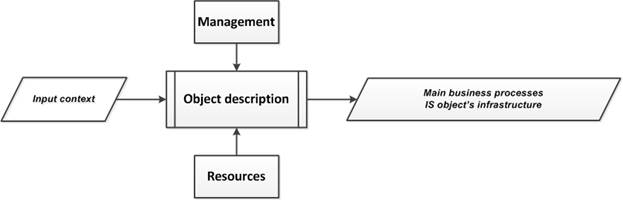
5.1. «Object description» subprocess
The purpose of the subprocess is to obtain data on the main business processes of the organization (those processes for implementation of which this organization was established) and about the features of the IS object that belongs to this organization. In this case, it is possible that the IS object is the organization as a whole.
There are the following typical IS objects:
1. An organization as a whole;
2. An information system as a set of information contained in databases and IT and technical tools providing its processing;
3. IT as processes, methods of information searching, collecting, storing, processing, presenting, disseminating and ways to implement such processes and methods;
4. An automated system as a system consisting of personnel and a set of tools automating its activities, which implements IT for the performance of established functions;
5. An informatization object as a set of information resources, tools and information processing systems used in accordance with the specified IT, as well as their maintenance tools, premises or objects (buildings, facilities, technical tools), in which these tools and systems are installed, or premises and objects for negotiation [9];
6. Technological processes implemented in the organization, usually using IT.
Input data of the subprocess (Fig.7) is the input context (external and internal) related to the organization and the IS object (Fig.6). The output of the subprocess or the output context (the description of the main business processes of the IS object and the description of the infrastructure of the IS object) are used as inputs for the next subprocess (Fig.6).
|
|
|
Fig. 7. Structural diagram of the “Object description” subprocess. |
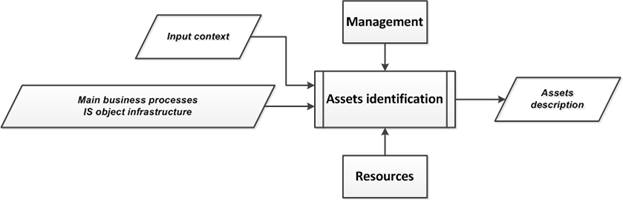
5.2. «Assets identification» subprocess
The purpose of the subprocess is a description of the IS objects, to ensure the security of which the ISS processes should be aimed. Such objects are assets as everything that has value for the organization [10]. In this case, only those assets that relate to the IS object and to the organization’s main business processes are considered.
There are the following asset types [4]:
a) Information: databases and data files, contracts and agreements, system documentation, research information, user guides, training materials, operation or support procedures, business continuity plans, emergency procedures, audit records and archived information;
b) Software: application software, system software, development tools and utilities;
c) Physical assets: computer equipment, communications, removable media and other equipment;
d) Services: computing services and communication services, basic support services such as heating, lighting, electricity and air conditioning;
e) Personnel, their qualifications, skills and experience;
f) Intangible values, such as the reputation and image of the organization.
If the processing information objects are concerned, the main assets will be information assets (IA) and assets related to the IA processing environment.
IA refers to information with the requisites (allowing it to be identified), having value for the organization, located at its disposal and presented on any physical medium in a form suitable for its processing, storage or transfer.
There are the following types of IA (determined on the basis of information classification):
1. Open (public) information.
2. Restricted access information (RAI):
2.1. Information classified as a specific type of secret (state, commercial, banking, service, medical, etc.).
2.2. Information attributed to Personally Identifying Information (PII).
2.3. Information that is classified as RAI by the decision of the organization’s management, for example:
· Information on the organization and its separate components;
· Information on the technologies used in the organization;
· Information on information processing tools;
· Management information of information and telecommunication systems (information used for technical configuration of software and hardware systems for information processing, storing and transferring).
An asset related to the IA processing environment (objects of IA processing environment) is a material object of the environment for the use and/or operation of the IA (storage, transmission, processing, destruction, etc. objects).
There are the following types of objects of IA processing environment:
1. Links and data transmission networks;
2. Software tools (general system, specialized);
3. Data files, databases, data stores;
4. Information carriers, including paper carriers;
5. Software and hardware components of information systems, automated systems and informatization objects;
6. Premises, buildings, structures;
7. Technological processes.
The objects of IA processing environment can be considered as separate assets to be protected.
The «Assets identification» subprocess consists of the following stages:
1. linking the asset to a specific main business process implemented by the organization;
2. binding of the asset to the IS object (to the infrastructure of the IA object);
3. description of the asset (determination of the asset type, its vulnerabilities and the IS properties to be protected with prioritization).
A vulnerability refers to a weakness of one or more assets, which can be used by one or more threats [10].
A vulnerability of the information system is a property of the information system, which makes it possible to implement threats to the security of information processed in it [9].
A vulnerability of an information asset is determined by a property that can be violated (confidentiality, accessibility, integrity), taking into account their priorities [2].
The properties of the asset represented by a separate object of IA processing environment are accessibility and integrity, taking into account their priorities.
The input data of the subprocess are the following (Fig.6, Fig.8):
· The input context (external and internal) related to the organization and the IS object;
· The output data of the "Object description" subprocess (output context), which contain a description of the main business processes of the organization and a description of the infrastructure of the IS object, as well as its relationships with the main business processes of the organization.
|
|
|
Fig. 8. Structural diagram of the “Assets identification” subprocess. |
The output of the subprocess (output context) includes the results of:
· linking the asset to a specific core business process implemented by the organization;
· binding of the asset to the infrastructure of the IA object;
· describing the asset (asset type, its vulnerabilities and IS properties to be protected with prioritization).
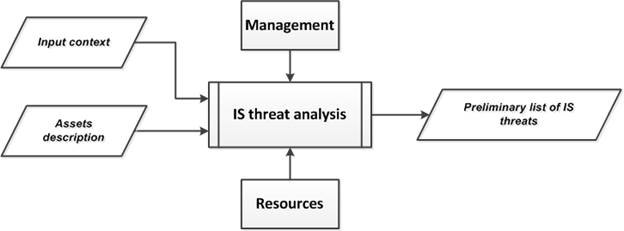
5.3. «IS threat analysis» subprocess
The purpose of the subprocess is the formation of a preliminary list of IS threats, specific to the organization and the IS object related to this organization.
IS threat is a set of conditions and factors that create a potential or actual danger of violating the IS properties of the IS object’s assets [9].
Each IS threat is associated with a certain asset and with the possibility of disrupting the IS properties of this asset, which can lead to damage to the organization.
The input data of the subprocess are the following (Fig.6, Fig.9):
· The input context (external and internal) related to the organization and the IS object (Fig.6);
· The output data of the "Assets identification" subprocess (output context), which describes the results of binding the asset to a certain main business process implemented by the organization, the description of the results of binding the asset to the infrastructure of the IA object and the results of the asset description.
|
|
|
Fig. 9. Structural diagram of the “IS threat analysis” subprocess. |
Within the framework of this subprocess, expert assessments are used to form a preliminary list of IS threats, based on the experience of ISMa of similar objects, as well as expert assessments of the applicability of typical IT threats listed in certain normative documents or published in various information sources.
The number of typical IS threats and their wording also depend on the level of generalization and the way threats are classified. For example, if the classification of threats is based on the types of their sources, the list of typical threats (TT) may look like this:
TT-1. Adverse events of a natural, technogenic and social nature.
TT-2. The activities of terrorists and perpetrators of crimes and offenses.
TT-3. Activities of suppliers/providers/partners.
TT-4. Software and hardware failures, malfunctions, destruction/damage.
TT-5. Activity of internal IS intruders.
TT-6. Activity of external IS intruders.
TT-7. Non-compliance with the requirements of supervisory and regulatory bodies, current legislation.
Expert assessment of this information allows to determine a preliminary list of IS threats, which refers to the output of the "IS threat analysis" subprocess (output context), which will be the input data of the next subprocess.
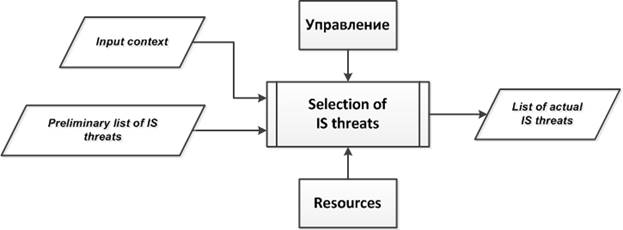
5.4. «Selection of IS threats» subprocess
The purpose of the subprocess is the formation of a list of actual IS threats, specific to the organization and the IS object related to this organization (Fig.6).
The input data of the subprocess are the following (Fig.6, Fig.10):
· The input context (external and internal) related to the organization and the IS object (Fig.6);
· The output data of the "IS threat analysis" subprocess (output context), which contain a preliminary list of IS threats.
The output data of the subprocess is a list of actual IS threats (Fig.6, Fig.10).
|
|
|
Fig. 10. Structural diagram of the “Selection of IS threats” subprocess. |
Risk assessment methods are used to select IS threats (form a list of actual IS threats), where risk is a probability of causing harm in view of its severity.
As an indicator of the urgency of the IS threat, a two-component vector characterizing the level of IS risk can be applied:
[ Rj ] = [ Pj, Xj ],
where
Ðj – a component characterizing the probability of the j-th IS threat;
Õj – a component characterizing the degree of possible damage to the organization in the event of its implementation.
Recommendations for building a methodology for assessing IS threats are given in [7].
For assessing risks for each IS threat it is necessary to:
· Choose a risk assessment methodology;
· To determine an acceptable risk of violation of the organization’s main business processes (so-called "risk-appetite", Ra) in the implementation of specific IS threats from the preliminary list of IS threats;
· To assess the risks for each IS threat from the preliminary list of IS threats – Rnj;
· To form a list of actual IS threats, which will include IS threats, for which the condition Rnj> Raj is fulfilled.
The output data of the subprocess (list of actual IS threats) is a part of the input data of the next subprocess.
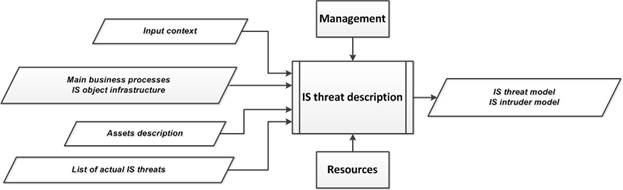
5.5. «IS threat description» subprocess
The purpose of the subprocess is the development of the IS threat model and the IS intruder model.
The input data of the subprocess are the following (Fig.6, Fig.11):
· The input context (external and internal) related to the organization and the IS object;
· The output data of the "Object description" subprocess (output context), which contain a description of the organization’s business processes and a description of the infrastructure of the IS object;
· The output data of the "Assets identification" subprocess (output context), which contain the description of the assets with their binding to certain main business processes implemented by the organization, to the IS object’s infrastructure, as well as the description of the assets (types of assets, their vulnerabilities and IS properties to be protected with prioritization);
· The output data of the "Selection of IS threats" subprocess (output context), which contain the list of actual IS threats.
|
|
|
Fig. 11. Structural diagram of the “IS threat description” subprocess. |
The output data of the subprocess are the IS threat model and the IS intruder model.
The description of IS threats to the assets of the IS object can be performed in accordance with recommendations [7].
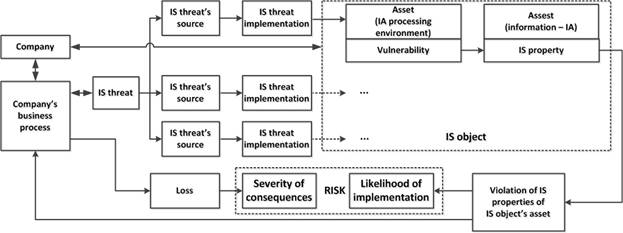
The description of a specific IS threat can be structured as follows [7]. The IS threat description stages are the following (Fig.12):
1. Selection of a threat from the list of actual IS threats;
2. Identification of sources of this IS threat;
3. Definition of the method of IS threat implementation;
4. Definition of the object (s), to which the IS threat is directed;
5. Determination of a possible type of violation of IS properties for IS object’s assets;
6. Risk assessment based on the severity of the consequences from the implementation of the IS threat and the likelihood of its implementation.
|
|
|
Fig. 12. Structural diagram of the stages of the IS threat description. |
The source of the IS threat is an object or subject that implements IS threats by impacting the objects of IA processing environment. For a specific IS threat there may be several sources and they can be directed to different assets related to the IS object as a part of the organization (Fig.12).
There are the following typical types of sources of IS threats (defined by typical IS threats):
TS-1. Natural (TT-1);
TS-2. Technogenic (TT-1, TT-4);
TS-3. Social (TT-1);
TS-4. The subject (intruder) (TT-2, TT-3, TT-5, TT-6);
TS-5. Legal (TT-7).
Typical type of source of threats TS-2 has two varieties:
1. Technogenic external (failures, malfunctions, destruction of objects that are external to the IS object);
2. Technogenic internal (failures, malfunctions, destruction/damage of software and hardware related to the IS object).
Typical type of source of threats TS-4 has two varieties:
3. The internal intruder. The internal intruder has an authorized access to the asset, to which a specific IS threat is directed. The internal intruder, as a rule, is an employee of the organization. The exception is the employees of external organizations, receiving the temporary access rights to the asset with the purpose of carrying out routine maintenance at the IS object;
4. The external intruder. The external intruder does not have authorized access to the asset, to which a specific IS threat is directed. The external intruder can be an employee of the organization or cannot work in this organization.
If the source of the IS threat is a subject (an intruder), then the IS intruder model should be developed.
The "IS threat description" subprocess has to do with the development of a model of those IS threats that are considered actual (see the "IS risk assessment" subprocess. Therefore, all these threats correspond to a risk that is considered "unacceptable".
Within the subprocess, the value of the risk for each threat in numerical terms should be determined.
The list of the above stages of describing a specific IS threat defines the structure of the IS threat model.
If the source of IS threat is anthropogenic, then the IS intruder model for such a source is developed in addition to the IS threat model.
In this case, it is possible to suggest the structure of the IS intruder model:
1. The source of IS threat (subject);
2. The intruder’s type (according to a location of the intruder with respect to the relevant asset – external or internal);
3. Identification of the asset affected by the source of IS threat;
4. Identification of ways to implement the IS threat;
5. Description of the level of access to the asset;
6. The intruder’s motivation;
7. The intruder’s qualification and/or resources.
It should be noted that the structure and content of the IS threat model and the IS intruder model should be consistent and not contradictory.
The IS threat model and the IS intruder model contain data related to the output context of the "IS threat analysis" subprocess and are used as the input data (input context) for subsequent subprocesses.
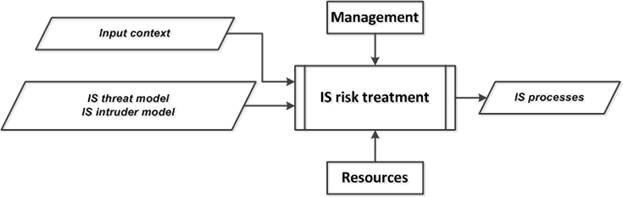
5.6. «IS risk treatment» subprocess
The purpose of the subprocess is to identify the ISMa processes, the implementation of which will ensure that risks are reduced to an acceptable level.
IS risk treatment refers to the process of changing the IS risk, aimed at selecting and implementing measures to reduce, retain, transfer or avoid IS risk.
IS risk reduction refers to the actions taken to lessen the probability, negative consequences, or both, associated with a risk [7].
IS risk retention refers to taking the burden of losses from a specific IS risk [7].
IS risk transfer refers to sharing with another party the burden of loss or benefit of gain, for a risk. IS risk transfer can be carried out by insurance or other agreements [7].
IS risk avoidance refers to a decision not to become involved in, or action to withdraw from, a risk situation. The decision can be made on the basis of the results of assessing the IS risk (comparing the achieved level of risk with the level of acceptable risk (risk appetite)) [7].
In this article, we consider the aspects of reducing the IS risk through the application of IS controls (ISMa measures) in the implementation of the IS processes.
The input data of the "IS risk treatment" subprocess are the following (Fig.6, Fig.13):
· The input context (external and internal) related to the organization and the IS object;
· The output data of the "IS threat description" subprocess (output context), containing the description of IS threats in the form of the IS threat model and the IS intruder model.
The output data of the subprocess is a list of IS processes and an IS risk registry.
|
|
|
Fig. 13. Structural diagram of the “IS risk treatment” subprocess. |
In accordance with the ISMaS structure (Fig.3), the ISMa processes form the ISS, which unites these processes and ISMa measures (IS controls), as well as the resources needed to implement these processes. In the general case, the number of such ISMa processes included in the ISS is M (Fig.3).
As an example, the following list of typical ISS processes can be proposed:
TP-1 "ISMa for access control";
TP-2 "ISMa for computer networks";
TP-3 "Control of the integrity and security of the IS object’s infrastructure";
TP-4 "Protection against malicious code";
TP-5 "Prevention of information leaks";
TP-6 "Protection of computer storage media";
TP-7 "IS incident management";
TP-8 "ISMa for virtualization environment";
TP-9 "ISMa in the implementation of remote logical access using mobile (portable) devices";
TP-10 "ISMa in the use of cryptographic tools."
Some of these typical ISS processes have their own subprocesses.
Taking into account the typical ISS processes described above, the "IS risk treatment" subprocess is implemented in the following order for each j-th IS threat from the list of actual IS threats (Fig.14):
1. Selection of information from the IS threat model, related to the description of the j-th IS threat. At the same time, the level of the initial risk Rnj is distinguished, which is estimated as unacceptable, and the level of risk appetite Raj;
2. Selection of the IS process and evaluation of a residual risk, which leads to the implementation of the chosen ISMa process. When choosing the ISMa process, it is necessary to take into account the characteristics of the IS threat’s source, the description of its implementation method, the characteristics of the object to which the IS threat (the asset and its vulnerability) is directed, as well as the consequences from the implementation of IS threats;
3. Repetitions of stage 2 until the selected processes provide a reduction of the residual risk to a level no higher than the risk appetite. In this case, it may be sufficient to implement one or several ISS processes for a specific IS threat;
4. Formation of an IS risk registry. The risk registry for each j-th IS threat includes a description of the following:
· The source of IS threat;
· The method of implementation of IS threat;
· The assets as objects of IS threat’s implementation (IA, asset related to the IA processing environment – IAPEA);
· The consequences from the implementation of the IS threat (for IA and for IAPEA);
· The risk assessment results – determination of the initial risk Rnj based on the assessment of the likelihood of the IS threat’s implementation and the assessment of the potential damage to the organization in the IS threat’s implementation;
· The chosen ISMa process (processes);
· The results of the reassessment of risk – determination of the residual risk Rîj on the basis of the assessment of the likelihood of the IS threat’s implementation and evaluation of the potential damage to the organization in the implementation of the IS threat, if the chosen ISMa process (processes) are implemented at the IS object.
|
|
|
Fig. 14. Stages of the “IS risk treatment” subprocess. |
It should be noted that the risk assessments carried out within the framework of the implementation of the "IS risk treatment" subprocess are preliminary. The final risk assessment will be carried out at the "Designing" stage of specific ISS processes, where the ISMa measures (IS controls) that implement the process are selected (Fig.4b, Fig.5b).
5.7. «IS Policy development» subprocess
The purpose of the subprocess is the development of the "IS Policy of the IS object" document.
In accordance with the recommendations of the standard [4], it is possible to define the "IS Policy" term and the structure of the IS policy description.
IS maintenance policy (IS Policy) refers to:
· a set of requirements and rules for IS object’s ISMA, developed in accordance with the requirements of guidelines and regulatory documents in order to counter a set of IS threats, taking into account the value of the protected information sphere;
· a regulatory document that defines the requirements for ISMa, a system of measures, or the procedure for actions, as well as the responsibility of the organization’s employees and control mechanisms for a certain area of ISMa.
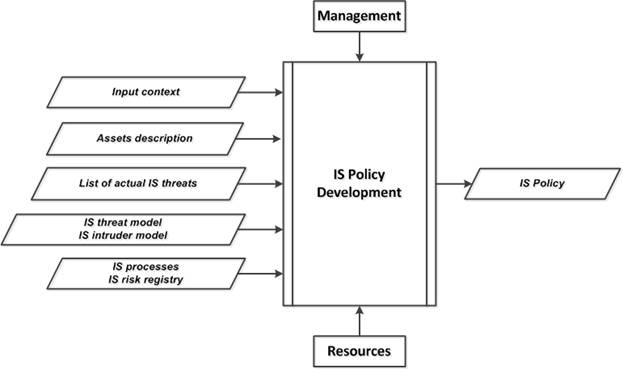
The input data of the subprocess are the following (Fig.6, Fig.14):
· The input context (external and internal) related to the organization and the IS object;
· The output data of the "Object description" subprocess, containing the description of the main business processes of the organization and the description of the IS object’s infrastructure;
· The output data of the "Assets identification" subprocess, containing the description of the assets (IA, IAPEA), including IA and IAPEA vulnerabilities, linked to the main business processes of the organization and to the IS object’s infrastructure;
· The output data of the "IS threat selection" subprocess, containing the list of actual IS threats;
· The output data of the "IS threat description" subprocess, containing the description of IS threats in the form of the IS threat model and the IS intruder model;
· The output data of the "IS risk treatment" subprocess, containing the IS risk registry and the list of ISMa processes (ISS processes) that counteract the implementation of IS threats and, as a result, reduce the residual risks to a level not higher than the risk appetite.
The output of the subprocess (output context) is the "IS Policy for the IS object" document (Fig.6, Fig.15).
|
|
|
Fig. 15. Structural diagram of the “IS Policy development” subprocess. |
The IS policy development stages are the following:
1. Definition of the type of IS policy. The IS policy, developed within the ISMS management process, related to the "Planning" of the ISMaS of the IS object as a single process, is the "IS Policy for the IS object" document;
2. Planning the development of the "IS Policy for the IS object" document and determining its structure;
3. Filling the sections of the "IS Policy for the IS object" draft document with a specific content;
4. Revision of the "IS Policy for the IS object" draft document;
5. Coordination and approval of the "IS Policy for the IS object" document.
The IS policy development can be built on the basis of the Shuhart-Deming model usage (Fig.2): "Planning (Stage 1 and Stage 2) — "Implementation" (Stage 3) — "Check" (Step 4) — "Action" (Stage 5).
The result of the implementation of the subprocess is the agreed and approved "IS Policy for the IS object" document.
5.8. «Internal IS documents development» subprocess
The purpose of the subprocess is the development of a set of the IS object’s internal documents on ISMa.
The input data of the subprocess are the following (Fig. 5):
· The input context (external and internal) related to the organization and the IS object;
· Information from the "IS Policy for the IS object" document (the output data of the "IS Policy development" subprocess);
· The results of the description of the actual IS threats to the IS object (the "IS threat description" subprocess).
The output data of the subprocess is a set of internal documents developed, agreed and approved by the management of the organization, related to the IS object’s ISMa.
This set also includes the "IS Policy for the IS object" document and the description of IS threats to the IS object (for example, in the form of the IS threat model and the IS intruder model).
This set of documents should contain the normative documents with requirements for all ISMa processes, as well as for the implementation, operation, control and improvement of ISMaS. The form of presentation can be the private IS policies, regulations, instructions, etc.
The normative documents’ content adds to the internal context related to the IS object.
This subprocess completes the development of ISMaS.
6. Conclusion
IS analytics makes it especially urgent to solve problems of analysis and visualization of information on the main processes of the object’s ISMaS.
Defining the structural diagrams of the subprocesses, which constitute a single process of the object’s ISMaS, allowed to determine the composition of data at the input and output of each subprocess. At the same time, the consistency of data relating to different subprocesses is achieved. This allowed us to solve the task of generating data intended for visualization of IS management processes. Thus, the presented work gave an answer to the question "What should I visualize?" within the framework of automation of the IS management process. There are no analogues of the presented research both in Russia and abroad in the open press, therefore the ideas presented are of undoubted interest for the scientific community.
Further development of the results presented in this article will be related to the choice of a single format for presenting data on the processes of managing the object’s IS and developing a visualization algorithm for these processes that will determine the further choice of tools, platforms and software to create a system for visual analysis of the IS management processes. At this initial stage of the study, this choice is not possible.
References
[1] Miloslavskaya N.G., Tolstoy A.I., Birjukov A.I. Information Visualization in Information Security Management for Enterprise’s Information Infrastructure. Scientific Visualization, 2014, Vol. 6, ¹ 2. Pp. 74-91.
[2] ISO/IEC 27000:2016 «Information technology. Security techniques. Information security management systems. Overview and vocabulary».
[3] ISO/IEC 27001:2013 «Information technology. Security techniques. Information security management systems. Requirements».
[4] ISO/IEC 27002:2012 «Information technology. Security techniques. Code of practice for information security management».
[5] ISO/IEC 27003:2017 «Information technology. Security techniques. Information security management systems. Guidance».
[6] ISO/IEC 27004:2016 «Information technology. Security techniques. Information security management. Monitoring, measurement, analysis and evaluation».
[7] ISO/IEC 27005:2011 «Information technology. Security techniques. Information security risk management».
[8] ISO/IEC 27006:2015 «Information technology. Security techniques. Requirements for bodies providing audit and certification of information security management systems».
[9] GOST R 50922-2006 «Information security. Main terms and definitions».
[10] ISO/IEC 13335-1:2004 «Information technology. Security techniques. Management of information and communications technology security. Part 1: Concepts and models for information and communications technology security management».
[11] ISO 9000:2015 «Quality management systems. Fundamentals and vocabulary».
[12] Niv G. Space of Doctor Deming. Moscow, Alpina Business Books. 2007.
[13] Bank of Russia Standard STO BR IBBS-1.0-2014 «Maintenance of Information Security of the Russian Banking System Organizations. General Provisions».
[14] GOST R 57580.1-2017 «Security of financial (banking) operations. Protection of information of financial organizations. Basic composition of organizational and technical measures».
[15] ISO/IEC TR 19791:2010 «Information technology. Security techniques. Security assessment of operational systems».